Arctic Access Control
Access control lets you manage and regulate access to Arctic catalogs and the objects and data they contain by determining who can access specific objects and what actions or operations they can perform on those objects.
Access control mechanisms are fundamental to preventing unauthorized access, enforcing security policies, minimizing risks, protecting sensitive information, maintaining compliance with regulations, and ensuring that users have the appropriate level of access based on their roles and responsibilities within an organization.
Privileges
Use role-based access control (RBAC) privileges to manage which users and roles can access Arctic catalogs and the folders, tables, and views they contain, as well as the actions they can take on the catalogs, folders, tables, and views. You can configure and manage Arctic catalog privileges in the Dremio console and grant privileges on a per-user or per-role basis.
By default, the organization owner and the catalog owner have all privileges on an Arctic catalog and the folders, tables, and views it contains. All other users must be granted privileges on the Arctic catalog and its folders, tables, and views by the organization owner, the catalog owner, or a user with the MANAGE GRANTS privilege.
Granting Privileges
Arctic catalog, folder, table, and view owners, users and roles that belong to the ADMIN role, and the organization owner can grant privileges to other users and roles in the Dremio console or with the GRANT TO USER and GRANT TO ROLE SQL commands.
See Transferring Ownership to learn how to manage OWNERSHIP for an Arctic catalog, table, or view.
Grant Privileges on an Arctic Catalog
To grant privileges on an Arctic catalog in the Dremio console:
-
On the Organization home page, click the Arctic tile.
-
Find the card that represents the Arctic catalog whose privileges you want to update.
-
Click
 in the top-right corner of the catalog card.
in the top-right corner of the catalog card. -
Select the Privileges tab in the catalog settings sidebar.
-
In the search field under Add User/Role, enter the name of a user or role.
-
In the list of search results, click to select the user or role that you want to assign privileges for.
-
Click the Add to Privileges button.
-
Select the checkboxes for the desired privileges you want to assign for each user or role.
-
Click Save.
Grant Privileges on a Folder in an Arctic Catalog
To grant privileges on a folder in an Arctic catalog or source:
-
Open the folder and click
 at the top-right corner of the page.
at the top-right corner of the page. -
In the search field under Add User/Role, enter a username or role. In the list of search results, click to select the user or role that you want to assign privileges for.
-
Click the Add to Privileges button.
-
Select the checkboxes for the desired privileges you want to assign for each user or role.
-
Click Save.
Grant Privileges on a Table or View in an Arctic Catalog
To grant privileges on a table or view in an Arctic catalog or source:
-
Click
 at the right side of the row for the table or view in the Arctic catalog or source.
at the right side of the row for the table or view in the Arctic catalog or source. -
Select the Privileges tab in the dataset settings sidebar.
-
In the search field under Add User/Role, enter a username or role. In the list of search results, click to select the user or role that you want to assign privileges for.
-
Click the Add to Privileges button.
-
Select the checkboxes for the desired privileges you want to assign for each user or role.
-
Click Save.
Revoking Privileges
Arctic catalog, folder, table, and view owners, users and roles that belong to the ADMIN role, and the organization owner can revoke privileges from other users and roles in the Dremio console or with the REVOKE FROM USER and REVOKE FROM ROLE SQL commands.
Revoke Privileges on an Arctic Catalog
To revoke privileges on an Arctic catalog in the Dremio console:
-
On the Organization home page, click the Arctic tile.
-
Find the card that represents the Arctic catalog whose privileges you want to update.
-
Click
 in the top-right corner of the catalog card.
in the top-right corner of the catalog card. -
Select the Privileges tab in the catalog settings sidebar.
-
To revoke only some privileges for a user or role, uncheck the checkboxes for the privileges you want to revoke.
-
To revoke all privileges for a user or role, click
to the right of the user or role name and select Remove.
- In the Remove user/role? confirmation dialog window, click Yes.
-
-
Click Save.
Revoke Privileges on a Folder in an Arctic Catalog
To revoke privileges on a folder in an Arctic catalog or source:
-
Open the folder and click
 at the top-right corner of the page.
at the top-right corner of the page.-
To revoke only some privileges for a user or role, uncheck the checkboxes for the privileges you want to revoke.
-
To revoke all privileges for a user or role, click
to the right of the user or role name and select Remove.
- In the Remove user/role? confirmation dialog window, click Yes.
-
-
Click Save.
Revoke Privileges on a Table or View in an Arctic Catalog
To revoke privileges on a table or view in an Arctic catalog or source:
-
Click
 at the right side of the row for the table or view in the Arctic catalog or source.
at the right side of the row for the table or view in the Arctic catalog or source. -
Select the Privileges tab in the dataset settings sidebar.
-
To revoke only some privileges for a user or role, uncheck the checkboxes for the privileges you want to revoke.
-
To revoke all privileges for a user or role, click
to the right of the user or role name and select Remove.
- In the Remove user/role? confirmation dialog window, click Yes.
-
-
Click Save.
Inheritance
In the Arctic inheritance model, granting privileges on a parent object like an Arctic catalog or a folder in an Arctic catalog also gives that user the same privileges on any objects in the parent object and any objects that are created in the parent object in the future (with the exception of the SHOW privilege on folders). For example, granting privileges to a user on an Arctic catalog gives that user the same privileges on any existing folders, tables, and views in the catalog. The user also has the same privileges on any folders, tables, and views that are created in the catalog in the future.
The SHOW privilege is only available on folders and is NOT inherited for any subfolders, tables, or views in a folder on which SHOW is granted.
Even if users have a direct privilege on a table or view, they must have the SHOW or SELECT privilege on the parent folder to navigate to the table or view in the Dremio console. For example, if Table 1 is saved in Folder 1, a user who has the SELECT privilege on Table 1 cannot navigate to Table 1 unless the user also has the SHOW or SELECT privilege on Folder 1.
To ensure that all users can navigate to any table or view on which they have a direct privilege, run the following SQL command:
GRANT SHOW ON ALL FOLDERS IN CATALOG <catalog_name> TO ROLE "PUBLIC"
Users must have the USAGE privilege at the catalog level to view, query, or alter any objects the catalog contains. Even if a user only requires privileges on a single table, they must also have the USAGE privilege on the Arctic catalog that contains the table. In addition to USAGE on the catalog, additional privileges are required for operations on the catalog's child folders and datasets.
Scope
Scope refers to the objects a user or role can access. By the rules of inheritance, you can grant privileges on Arctic catalogs and their objects as high or low in the object hierarchy as you wish. Privileges assigned at the catalog level determine the actions users and roles can take for the catalog and the objects it contains. Privileges granted on an individual table or view mean that user/role access only extends to that dataset, not to the parent folder or other datasets created in the same folder. If a user only needs privileges on a single object, you need only grant privileges on that object.
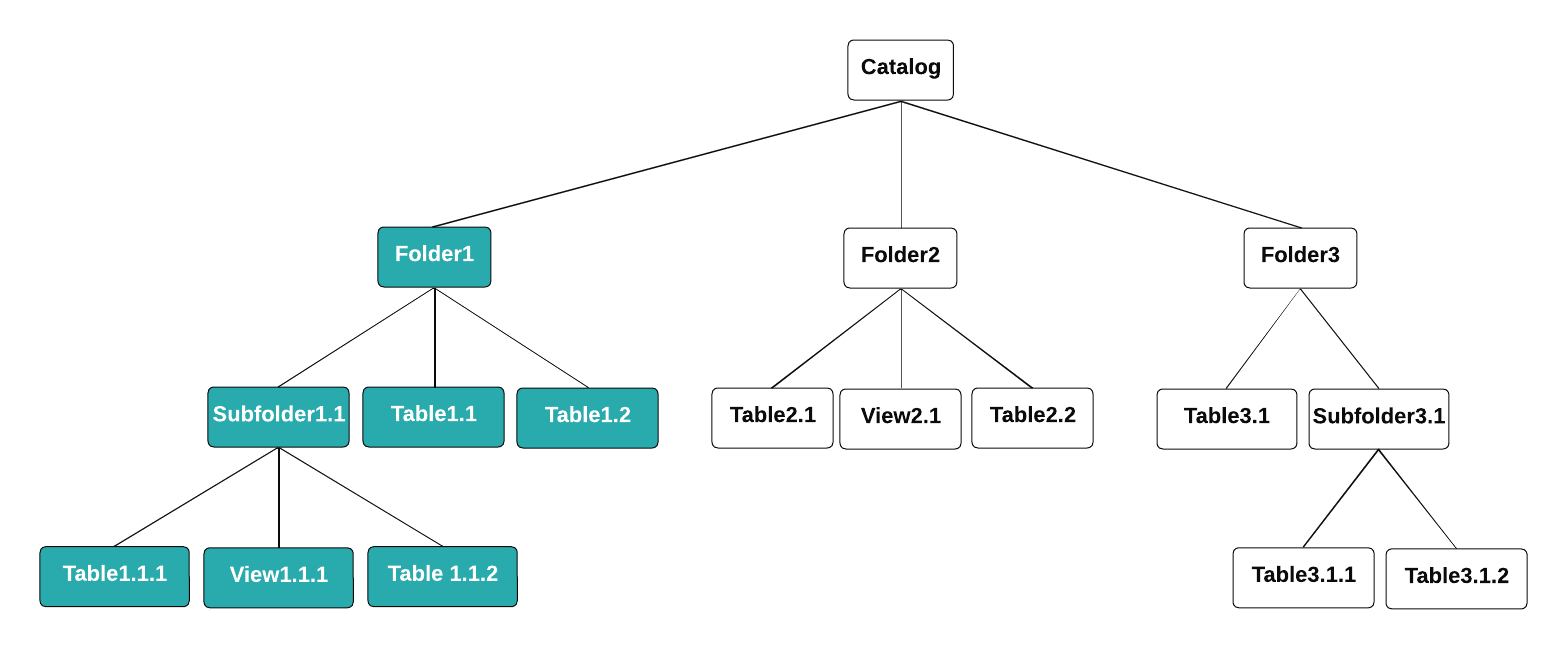
For example, suppose a user is granted certain privileges on a single folder in an Arctic catalog, and the catalog contains several other folders. As shown in the following diagram, that user has the same privileges on Folder1 and all of the objects Folder1 contains. Due to the inheritance model, the user also has the same privileges on any objects that are created in Folder1 in the future. The user does not have privileges on Folder2 or Folder3, nor any of their contents. The scope of the user's access is Folder1:
If the user should be able to run SELECT queries on all of the tables and views in the catalog, including any created in the future, you can grant them the USAGE and SELECT privileges at the catalog level. The user won't be able to access or query other Arctic catalogs or the objects other catalogs contain:
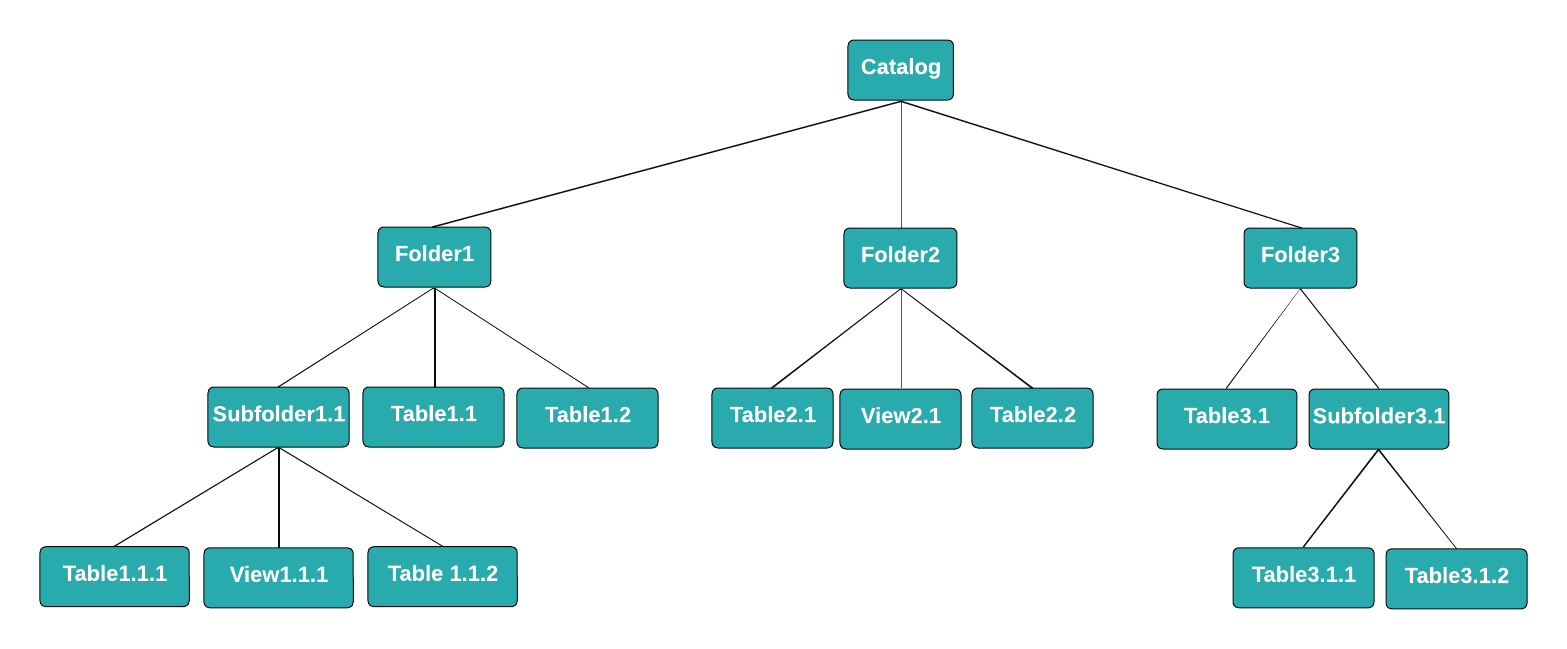
If the user should be able to run queries only on Table1.1, you can grant them the USAGE privilege on the catalog and the SELECT privilege only on Table1.1. The user won't be able to access or query any other tables or views in the catalog. However, the user will be able to create views based on Table1.1, and they can then grant privileges on the views they create to other users:

Privileges that are granted on a table or view on any branch in an Arctic catalog apply to all branches where the table or view exists. For example, suppose Table1 exists on the main, staging, and qa branches of Catalog1. If a user is granted the SELECT privilege on Table1 on the main branch, that user also has the SELECT privilege on Table1 on the staging and qa branches.
Ownership
Each Arctic catalog and each object the catalog contains has only one owner. Ownership is granted to the catalog or object's creator by default. The owner can transfer ownership to another user or role.
Ownership of an Arctic catalog does not extend to ownership of the objects in the catalog. For example, suppose the user Alice creates Catalog1 and grants all privileges on the catalog to the user Bob. Bob then creates Table1 inside Catalog1. In this scenario, Bob is the owner of Table1, not Alice. As the catalog owner, Alice has all privileges on Table1, but she is not its owner.
The ownership privilege is scoped and hierarchical. The owner of an Arctic catalog can change the owners of the objects within the catalog (and do anything else with the catalog's objects, including modify object settings and drop or delete objects).
View Delegation
Tables with restricted access may be used with greater access through the creation of a view. When a user with SELECT access to a table creates a view, that user automatically becomes owner of the new view. They have the ability to query and alter settings or data as desired. However, changes made to the view will not affect the original table.
View delegation means that queries use the view owner to query all underlying datasets. For queries that call a view within a view, the query switches the owner to the original view's owner as it queries the view's downstream objects.
Upon creating the view, the same rules of ownership described above apply. The owner or delegation identity does not change when a view is edited or queried but must be manually changed via the GRANT TO USER or GRANT TO ROLE commands. To identify the owner of a view, follow the steps in Viewing Ownership.
The shared view still selects from the underlying dataset using the view owner's permissions, even if the end user querying the view lacks privileges to modify the underlying table. This applies to each table and view on the data graph and chain of datasets.
Viewing and Transferring Ownership
Arctic catalog, folder, table, and view owners can transfer their ownership to another user or role in the Dremio console or with the GRANT TO USER and GRANT TO ROLE SQL commands.
Owners can also use the Dremio console to view and transfer ownership as described in the sections below.
Ownership transfers take effect immediately, and catalogs, folders, tables, and views have only one owner. Only the user or role to which you granted ownership, users and roles that belong to the ADMIN role, and the organization owner can make ownership changes.
Using the Dremio Console to View and Transfer Ownership on an Arctic Catalog
To use the Dremio console to view and transfer ownership on an Arctic catalog to another user or role:
-
On the Organization home page, click the Arctic tile.
-
Find the row (for list view) or card (for card view) that represents the Arctic catalog whose ownership you want to view. The owner is listed in the Owner column (for list view) or in the card (for card view).
-
Click
 at the right side of the row or in the top-right corner of the catalog card.
at the right side of the row or in the top-right corner of the catalog card. -
Select the Privileges tab in the catalog settings sidebar.
-
At the top of the Privileges page, click Transfer Ownership. A search field appears under Owner.
-
In the search field under Owner, find the user or role to which you want to transfer ownership and click the user or role name to select it.
-
Click Transfer.
-
In the Transfer ownership to this user/role? confirmation dialog, click Transfer.
Using the Dremio Console to View and Transfer Ownership on a Folder in an Arctic Catalog
To view and transfer ownership on a folder in an Arctic catalog to another user or role:
-
Open the folder and click
 at the top-right corner of the page. The owner is listed at the top of the Folder Settings page.
at the top-right corner of the page. The owner is listed at the top of the Folder Settings page. -
At the top of the Folder Settings page, click Transfer Ownership. A search field appears under Owner.
-
In the search field under Owner, find the user or role to which you want to transfer ownership and click the user or role name to select it.
-
Click Transfer.
-
In the Transfer ownership to this user/role? confirmation dialog, click Transfer.
Using the Dremio Console to View and Transfer Ownership on a Table or View in an Arctic Catalog
To view and transfer ownership on a table or view in an Arctic catalog to another user or role:
-
Click
 at the right side of the row for the table or view in the Arctic catalog or source.
at the right side of the row for the table or view in the Arctic catalog or source. -
Select the Privileges tab in the settings sidebar. The owner is listed at the top of the Privileges page.
-
At the top of the Privileges page, click Transfer Ownership. A search field appears under Owner.
-
In the search field under Owner, find the user or role to which you want to transfer ownership and click the user or role name to select it.
-
Click Transfer.
-
In the Transfer ownership to this user/role? confirmation dialog, click Transfer.
View Delegation
View delegation means that tables with restricted access may be shared with other Dremio users through the creation of views. When a user with SELECT access to a table creates a view, that user automatically becomes the owner of the new view.
Upon creating the view, the same rules of ownership apply to the view. The owner or delegation identity does not change when a view is edited or queried, but must be manually changed via the GRANT TO USER or GRANT TO ROLE commands. To identify the owner of a view, query the sys.views table.
The shared view still selects from the underlying dataset using the view owner's permissions at the time of the view's last modification, even if the end user querying the view lacks privileges to modify the underlying table. This applies to each table on the data graph and chain of datasets.
View delegation is different from privilege assignment. View delegation is implicit delegation of the SELECT privilege on underlying objects. For example, suppose user1 has the SELECT privilege on Table1 and creates View1 based on Table1. If user1 grants the SELECT privilege on View1 to user2, then the SELECT privilege that user1 has on Table1 is implicitly granted to user2. user2 can see the data in Table1 even though they lack explicit SELECT privileges on Table1. Privilege assignment is an explicit delegation: the owner of an object or a user who belongs to the ADMIN role grants privileges on the object to other users.