Data Lake Authentication Options for AWS Glue Data Catalog
Project Data Credentials with Access Key/IAM Role
To authenticate using Project Data Credentials:
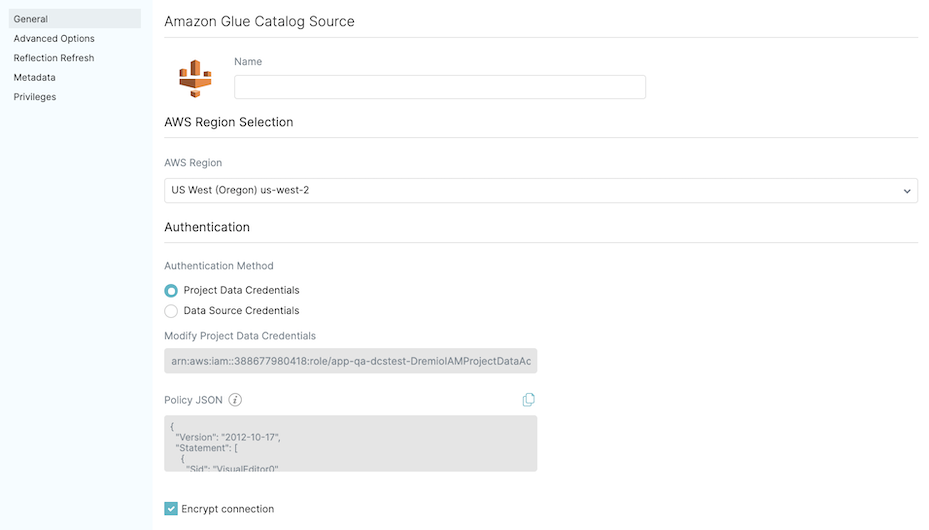
- For Authentication Method, select Project Data Credentials. The IAM role that is used in the project data is shown under Modify Project Data Credentials.
- Under Policy JSON, copy the Policy JSON template and append to the existing IAM policy associated with the project role/user shown in the previous step. Alternatively, you can create a new IAM policy and attach it to the project role/user. For steps on how to attach new permission policies to an existing IAM role/user, see setting up AWS IAM permissions. You can skip this step if you have already created a policy and attached it to the IAM role/user when you configured your AWS account.
Go back to the General tab configuration.
Data Source Credentials with Access Key
For authentication using Data Source Credentials with Access Key:
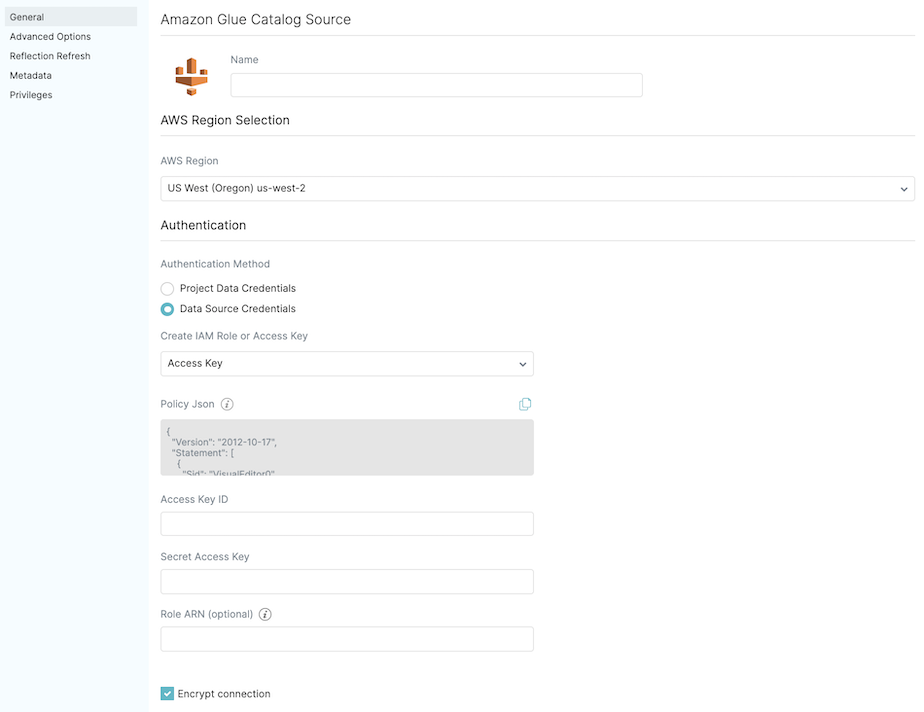
- For Authentication Method, select Data Source Credentials.
- For Create IAM Role or Access Key, select Access Key.
- For Policy JSON, use the JSON template to create an IAM user with Access Key. Attach a policy to access the Data Catalog source. For steps, see create an IAM user. You can skip this step if you have already created an IAM user when you configured your AWS account.
- For Access Key ID, enter the access key ID that is specific to the Data Catalog source.
- For Secret Access Key, enter the secret access key that is specific to the Data Catalog source.
- (Optional) For Role ARN, enter the ARN of the IAM role the access key should assume.
Go back to the General tab configuration.
Data Source Credentials with IAM Role
For authentication using Data Source Credentials with a new IAM role:
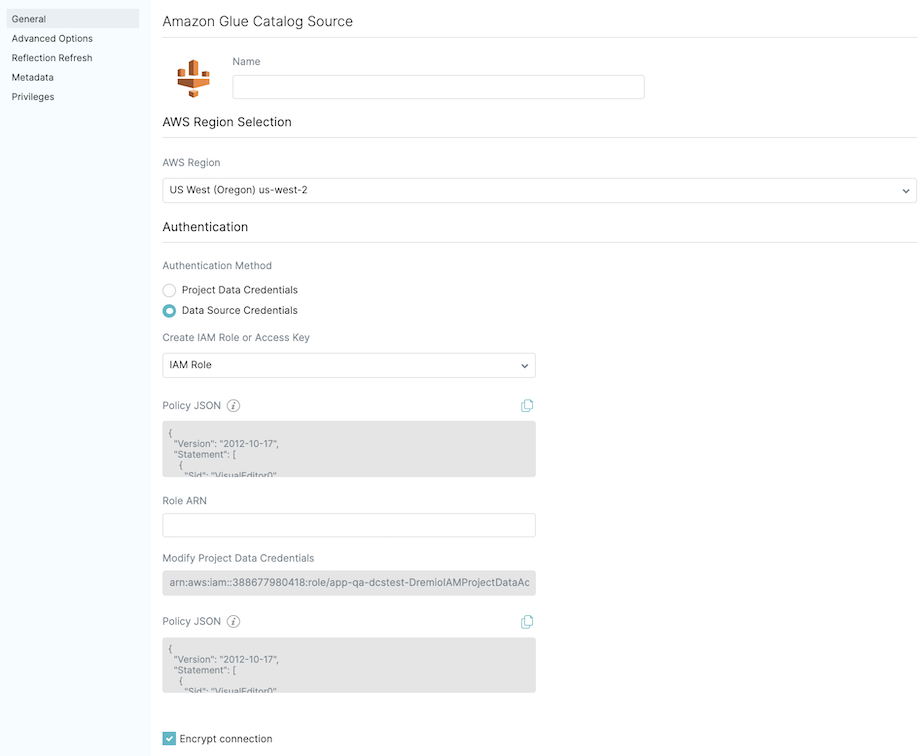
-
For Authentication Method, select Data Source Credentials.
-
For Create IAM Role or Access Key, select IAM Role.
-
For Policy JSON, use the JSON template to create an IAM role for the Data Catalog source. For steps, see create an IAM role. You can skip this step if you have already created an IAM role when you configured your AWS account.
-
For Role ARN, enter the role ARN for the source to assume the role.
-
Under Modify Project Data Credentials, the IAM role/user associated with the project is shown.
-
For Policy JSON, use the JSON template to modify the project data role/user shown in the previous step to give it permissions to assume the IAM role you created for this source. For steps on how to attach new permission policies to an existing IAM role, see setting up AWS permissions.