Azure Key Vault Enterprise
Use Dremio's Azure Key Vault integration to reference a secret rather than providing a password or other sensitive information when you connect to a data source or configure a Dremio configuration file.
Dremio must be deployed on Azure AKS to use the Azure Key Vault integration for secrets management.
After you complete the prerequisites, you can create secrets in Azure Key Vault and use them in Dremio. Dremio uses the secret references you provide to retrieve secret values at runtime and authenticate to data sources and other services.
Supported Data Sources
Dremio supports Azure Key Vault secrets for all data source types except Hadoop Distributed File System (HDFS), Hive 2.x and 3.x, and network-attached storage (NAS).
Supported Configuration Files and Properties
You can use an Azure Key Vault secret as the value for any of the configuration file properties listed in Encrypt Credentials.
Prerequisites
Dremio uses Azure managed identities to connect to Azure Key Vault. Create a user-managed identity for Dremio or select an existing user-managed identity previously created for Dremio. Note the Client ID of your managed identity.
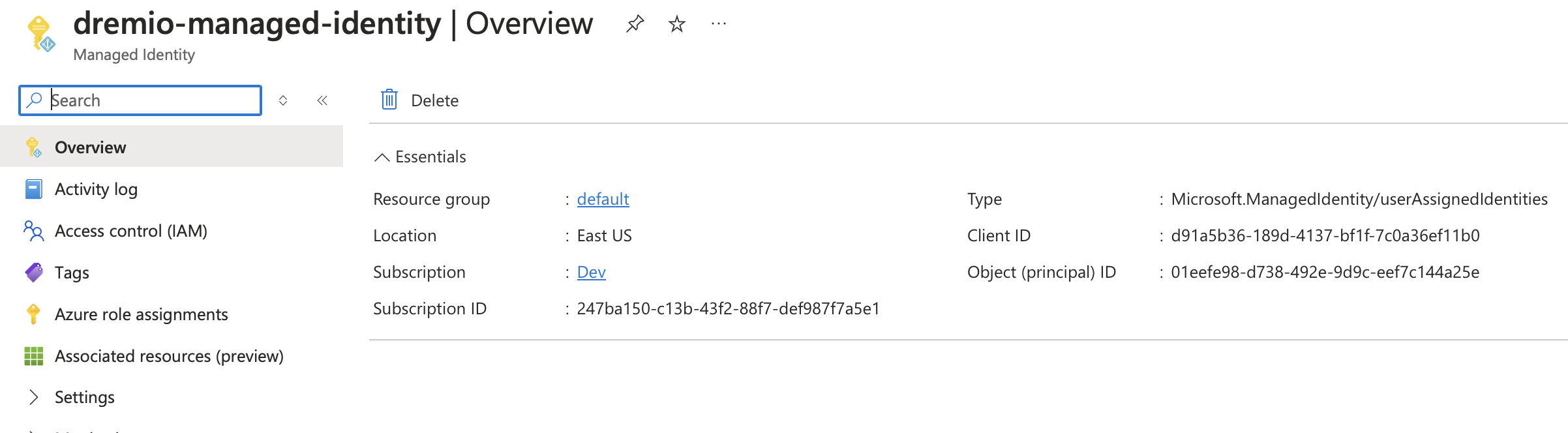
d91a5b36-189d-4137-bf1f-7c0a36ef11b0. To enable Dremio to connect to Azure Key Vault using your managed identity, complete the following steps:
- AKS
- Azure VMs
When deploying Dremio on a Kubernetes cluster in the Azure Kubernetes Service (AKS):
-
Assign the managed identity to the AKS cluster's Virtual Machine Scale Set (VMSS).
-
Provide access to Azure Key Vault using Azure RBAC access control or an Azure access policy. When using Azure RBAC, grant access to the Azure Key Value Secret User role.
-
Configure an environment variable for your Azure managed identity Client ID. Add the
Example configuration of Azure maanged identityAZURE_MANAGED_IDENTITY_CLIENT_IDenvironment variable to yourvalues-overrides.yamlfor thecoordinatorandexecutorwith the value of your Azure managed identity Client ID.coordinator:
extraEnvs:
- name: AZURE_MANAGED_IDENTITY_CLIENT_ID
value: d91a5b36-189d-4137-bf1f-7c0a36ef11b0
executor:
extraEnvs:
- name: AZURE_MANAGED_IDENTITY_CLIENT_ID
value: d91a5b36-189d-4137-bf1f-7c0a36ef11b0 -
Deploy new Dremio containers using your updated Helm chart.
When deploying Dremio on Azure virtual machines (VMs):
-
Assign the managed identity to each coordinator and executor VM.
-
Provide access to Azure Key Vault using Azure RBAC access control or an Azure access policy. When using Azure RBAC, grant access to the Azure Key Value Secret User role.
-
Edit the Dremio dremio-env file on the coordinator and each executor to add the
Example updates in dremio-envAZURE_MANAGED_IDENTITY_CLIENT_IDenvironment variable with the Client ID of your managed identity. Export this variable definition fromdremio-env.export AZURE_MANAGED_IDENTITY_CLIENT_ID="d91a5b36-189d-4137-bf1f-7c0a36ef11b0" -
Restart Dremio to use your updated
dremio-env.
Retrieving the Secret Reference from Azure Key Vault
The secret reference for an Azure Key Vault secret is the secret identifier URL, without the secret version number. The secret identifier is available on the secret's details page in the Azure Key Vault console.
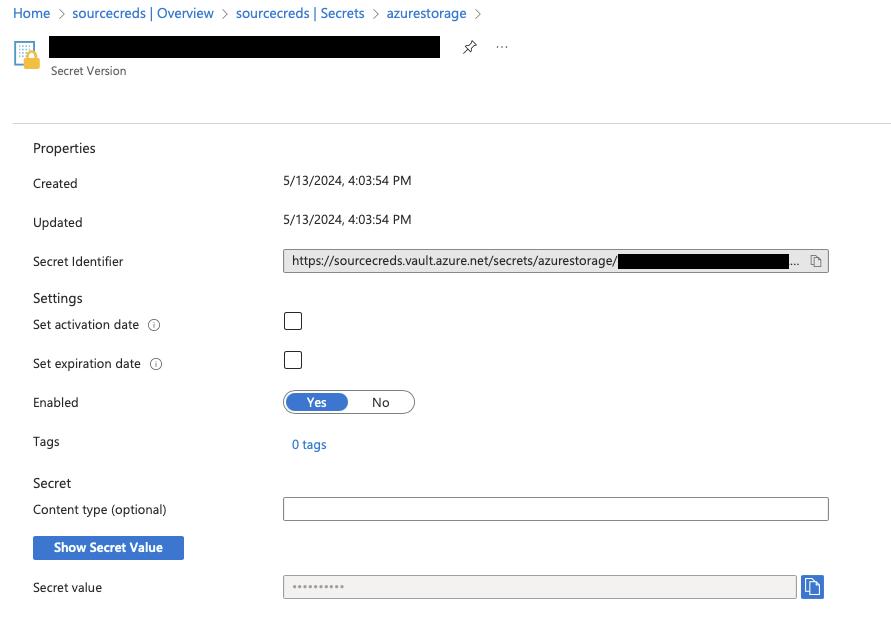
https://sourcecreds.vault.azure.net/secrets/azurestorage. Using A Secret Reference
Connecting to Data Sources
When you configure a new data source or edit the settings for an existing data source, enter the partial secret identifier URL for the Azure Key Vault secret directly into the corresponding password or secret key field in the Dremio console. If you configure a data source using the Dremio API, provide the partial secret identifier as the value for the corresponding parameter in your request body.
Dremio Configuration Files
In Dremio configuration files, use the partial secret identifier URL for the Azure Key Vault secret in place of a plaintext secret. You can use the partial secret identifier URL as the value for any of the configuration file properties listed in Encrypt Credentials.
You must add dremio+ as a prefix to secret references before using them in core-site.xml files. For example:
core-site.xml
dremio+https://sourcecreds.vault.azure.net/secrets/azurestorage
Secrets Rotation
For seamless rotation of secrets stored in Azure Key Vault, the rotation must be done with two secrets. After the Azure Key Vault secret value is updated, both secrets must remain valid for the minimum holdover period:
- Plain secrets: 5 minutes
- Microsoft Entra ID client secrets: 90 minutes
You may invalidate the old secret when the holdover period expires. It is not necessary to restart the Dremio coordinator when you rotate secrets stored in Azure Key Vault.