Privileges Enterprise
The following table shows all privileges currently supported by Dremio’s access control functionality.
All Supported Privileges
Dataset Privileges
| Privilege | Target Objects | Description |
|---|---|---|
| ALL | Source, Folder/Schema, Dataset/View | Grant the user all possible privileges for an object type, except MANAGE GRANTS and OWNERSHIP. |
| ALTER | System, Space, Source, Folder, Table, View | Add, delete, or modify table or view definitions, columns, or settings of all datasets in scope. For spaces, sources, tables, and views, this includes editing the wiki. For tables, this includes managing metadata, such as Metadata Refresh and Forget. |
| ALTER REFLECTION | System, Source, Space, Folder | Create, edit, and view Reflections on all datasets in scope. Includes granting access to all interfaces, such as the Dataset Reflection pages, Administrator Reflection pages, and any REST API endpoints. |
| CONFIGURE SECURITY | System | Configure security-related features for the system: enable single sign-on (SSO) for BI applications like Tableau and Power BI and configure Dremio to honor tokens issued by external identity providers. |
| CREATE_TABLE | System, Source, Folder | Create a table using CREATE TABLE AS SELECT (CTAS) for all datasets in the scope. |
| DELETE | System, Source, Space, Folder/Schema, Dataset/View | Execute the associated DML operation on all datasets in scope. This is only supported with Apache Iceberg datasets. |
| DROP | System, Source, Folder | Drop tables on any dataset in the scope. |
| INSERT | System, Source, Space, Folder/Schema, Dataset/View | Execute the associated DML operation on all datasets in scope. This is only supported with Apache Iceberg datasets. |
| MANAGE GRANTS | System, Source, Space, System Table, Folder, Table, View | Modifies the privileges of all objects in the set scope. |
| OWNERSHIP | Organization, Space, Source, Folder/Schema, Dataset/View, Users, Roles | Allows all actions on the object and objects within the object, except GRANT OWNERSHIP cannot be applied to ALL DATASETS. Actions include modifying object settings, granting/revoking user and role access, and deleting the object. |
| SELECT | Source, Space, System Table, Folder, View, Table | Gives the ability to execute SELECT queries in the scope. For Nessie tables, see the dataset definition. |
| TRUNCATE | System, Source, Space, Folder/Schema, Dataset/View | Execute the associated DML operation on all datasets in scope. This is only supported with Apache Iceberg datasets. |
| UPDATE | System, Source, Space, Folder/Schema, Dataset/View | Execute the associated DML operation on all datasets in scope. This is only supported with Apache Iceberg datasets. |
| VIEW REFLECTION | System, Source, Space, Folder | View table metadata and Reflections on all datasets in the scope. Includes access to all Dremio interfaces, such as the Reflections tab on the Edit Dataset page for the dataset, the Reflections sidebar in Settings, and any REST API endpoints. |
Script Privileges
| PRIVILEGE | DESCRIPTION |
|---|---|
| VIEW | Grants the privilege to view a script. |
| MODIFY | Grants the privilege to modify a script. |
| DELETE | Grants the privilege to delete a script. |
| MANAGE GRANTS | Grants the ability to grant or revoke privileges on a script. |
Sources & Spaces
| Privilege | Target Objects | Description |
|---|---|---|
| CREATE ROLE | System | Create new roles but does not include access to editing the admin role memberships. |
| CREATE SOURCE | System | Create new sources. |
| CREATE USER | System | Create new users. Assigning roles to the new users also requires the CREATE ROLE privilege. |
| EXTERNAL QUERY | System, Source | Run external queries on relational-database sources. See Querying Relational-Database Sources Directly. |
| MODIFY | System, Source, Space, Engine | Edit and delete an object. The following conditions apply:
|
| UPLOAD | System | Upload files to the home space. |
| VIEW JOB HISTORY | System | Give the ability to view all job history. |
User-Defined Function Privileges
| PRIVILEGE | DESCRIPTION |
|---|---|
| ALL | Grants the user all possible privileges for the function except MANAGE GRANTS and OWNERSHIP. |
| ALTER | Grants the ability to edit a function. |
| EXECUTE | Execute the associated function for the purposes of querying tables/view with row-access or column-masking policies applied. Users or roles must have this privilege in order to alter a table and provide row-access or column-masking policies. |
| MANAGE GRANTS | Grants the ability to grant or revoke privileges on a function. |
| OWNERSHIP | Assigns ownership of the function. |
Granting Privileges
You can share catalog objects with others in your organization by granting privileges. By default, a new user is assigned the PUBLIC role, which grants the user the USAGE privilege on all projects.
To grant additional privileges to roles or users, complete the following steps:
-
Locate the desired object.
-
Click
 or
or  depending on the object.
depending on the object. -
In the object settings dialog, select Privileges from the settings sidebar.
For some object types, the settings dialog automatically opens to display the privilege settings, and you do not need to select the Privileges tab.
-
In the Privileges dialog, enter the name of the user or role that you want to grant access to under Add User/Role.
-
Click Add to Privileges.
If the entry matches a user or role in Dremio, then a record will appear for them in the Users table.
-
In the Users table, toggle the green checkmark for each privilege you want to grant for that user or role. For a description of the privilege, hover over the column name in the Users table. See the example below:
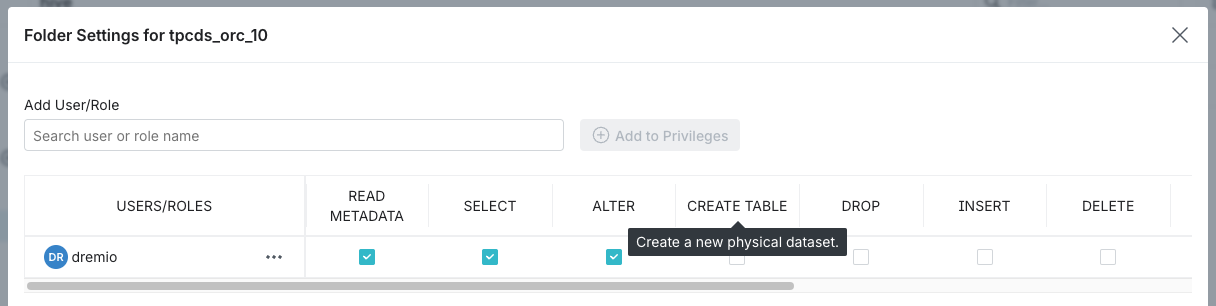 note
noteUse the pre-populated All Users row to grant privileges to the PUBLIC role.
-
(Optional) Repeat steps 2-4 if you want to add more users or roles and grant them privileges.
-
When finished, click Save.
Revoking Privileges
To revoke user and role privileges, complete the following steps:
-
Locate the desired object.
-
Click
 or
or  depending on the object.
depending on the object. -
In the object settings dialog, select Privileges from the settings sidebar.
noteFor some object types, the settings dialog automatically opens to display the privilege settings, and you do not need to select the Privileges tab.
-
In the Privileges dialog, locate the desired user or role record. If the user or role is not listed, then they do not have specific privileges on the object aside from any privileges listed in the All Users row, which represents the PUBLIC role.
-
Clear the checkboxes in the columns for the privileges you wish to revoke. For a description of the privilege, hover over the column name in the Users table. See the example below:

- When finished, click Save.
If a user has a specific privilege on an object through their memberships in multiple roles and the privilege is revoked for one of the roles, the user retains the privilege until it is revoked on the same object for all roles to which the user belongs.
You can also grant or revoke privileges using SQL commands or REST APIs.